
Fancy Bear – A Classy Threat Group
Fancy Bear is a Russian state-sponsored advanced persistent threat (APT) group that is also known by a number of other names, including APT28, Sofacy Group, and PawnStorm.
The group has been active since at least 2007, and its operations have been linked to a wide range of cyber espionage and cyber sabotage activities.
Background
Like Cozy Bear, Fancy Bear is also believed to operate under the auspices of Russia’s military intelligence agency, the GRU, and its activities are said to be focused primarily on furthering Russian strategic interests.
Techniques
The group is known for its use of sophisticated hacking techniques, including zero-day exploits, spear-phishing, and malware attacks.
In addition, Fancy Bear has been known to use a variety of different attack vectors and techniques, including the use of fake websites, social engineering tactics. For example they register domains that closely resemble those of legitimate organizations they plan to target in order to establish phishing sites that spoof the look and feel of the victim’s web-based email services, with the intention of harvesting their credentials.
They are also known for their ability to carry out attacks using multiple stages, with each stage designed to evade detection by security systems and remain undetected for as long as possible.
Fancy Bear has invested significant time in developing their primary implant, XAgent, as well as proprietary tools and droppers such as X-Tunnel, WinIDS, Foozer, and DownRange.
This implant has been ported across multiple operating systems for both conventional computers and mobile platforms.
Former Cases
Fancy Bear’s attacks have not been limited to the United States and Western Europe, but have been observed targeting victims across the globe in various sectors.
The group’s focus on defense ministries and other military victims closely mirrors the strategic interests of the Russian government.
For example, in 2015, the group was linked to the hack of the German parliament, or Bundestag, in which they gained access to sensitive information and reportedly remained undetected for months.
Fancy Bear has also been linked to the 2015 cyber attack on France’s TV5 Monde TV station, which caused significant disruption to the network’s broadcasting capabilities. The group used a multi-stage attack involving phishing emails, malware, and backdoors to gain access to TV5 Monde’s network and carry out the attack.
The group has also been observed targeting a wide range of other organizations and sectors, including media outlets, energy companies, and technology firms.
Bear VS. Hornet
During the beginning of the Russia-Ukraine conflict a new hacktivist group emerged named BlueHornet which unlike most hacktivist groups, decided to go for a crusade, targeting Russia’s top threat groups.
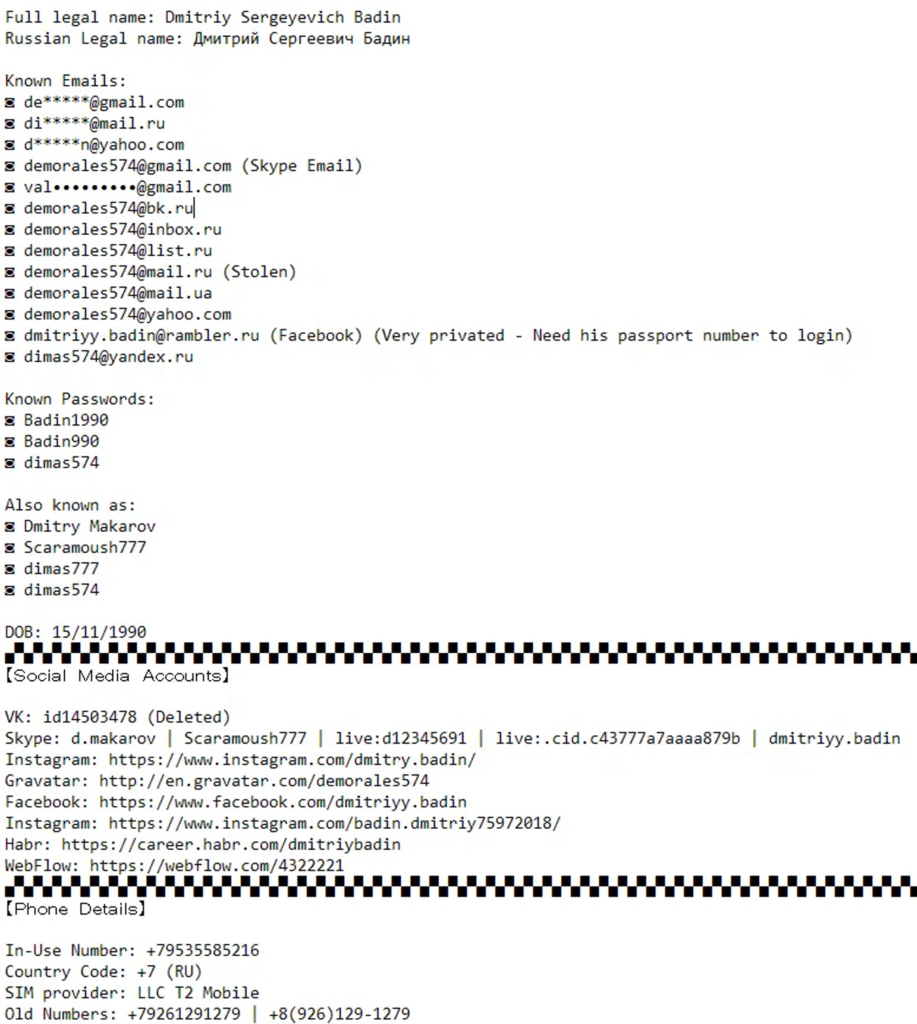
As one of their operations they were able to compromise and dox the full private information of Dmitriy Sergeyevich Badin, on of the members of Fancy Bear.
Although BlueHornet released all of his information, obviously no arrests were made.
Conclusions
As the name suggest Fancy Bear focuses on operations and espionage campaign that has huge impact on Russia’s opponents using the most advance and “fancy” techniques they have on their arsenal. Especially when i comes to long term campaigns that demands persistence and stealth.
Like other nation-state sponsored groups are pretty much unstoppable when it comes to law authorities and most states had their own “Fancy Bears” that do the dirty work for them.
The idea is that these individuals might be arrested only in cases were they leave Russia to a state where the FBI can get its hands on them and of course if their identity has been compromise.
