Introduction
OpenCTI is a great tool for threat intelligence. It can link and store huge amounts of data and give some really exciting insights about events, threat groups, vulnerabilities, and campaigns and is currently happening.
The Idea is, of course, to use this platform as an automatic entity that for starters at least, will import huge amounts of data that manually might take us months to import.
For that reason exactly we have the OpenCTI connectors.
I already covered the OpenCTI introduction in another blog so you are more then welcome to check that out!
What is a connector?
A connector, is a piece of software that allows you to connect various data sources to the platform. This can include data sources like threat intelligence feeds, vulnerability scanners, and incident response tools.
Connectors are used to import data from these external sources into OpenCTI, where it can be further analyzed, correlated, and used to inform security operations. Connectors can be used to automate the process of collecting data from various sources, which can save time and effort when compared to manually collecting data. They can also be used to standardize the format of data from different sources, making it easier to work with and analyze.
Additionally, connectors can be used to enrich the data in OpenCTI by adding additional information or context.
How To Install a New Connector
Installing connectors in OpenCTI is a straightforward, but first, where do we find connectors?
So here is the deal – OpenCTI project is maintaining a Notion page named OpenCTI Ecosystem that stores links to all the connectors that are currently available for the platform. Some of the connectors needs paid license but even if we want some free ones we can still find a lot of data that is very impactful.
To show how we can install a connector we will take an example for one of the connectors – MITRE Att&ck
In order to do so, we will clone the connectors github into our OpenCTI directory.
The repository includes tones of connectors for you to choose from so go nuts!
Every connector has a docker-compose.yml file that contain all the configuration needed for the connector to work properly (Figure 1).
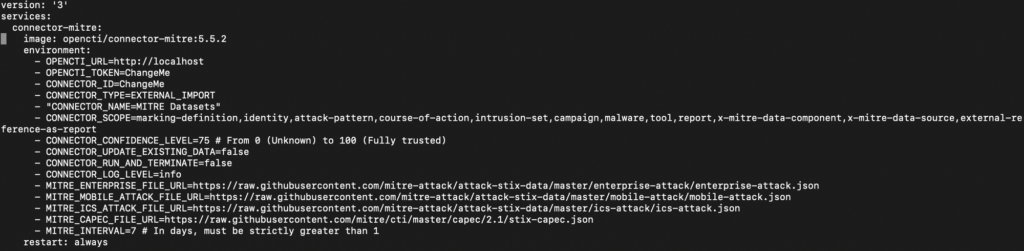
In MITRE’s case, we need to change the OPENCTI_URL, OPENCTI_TOKEN and CONNECTOR_ID.
Once we do it, we need to copy the connector-mitre data into the OpenCTI’s .yml file.
Adding the connector to the .yml file is not enough, we need to restart the OpenCTI docker file by using:
sudo docker-compose -f docker-compose.yml up
And thats about it! we have successfully added a new connector to our OpenCTI platform. But what connectors should we take?
8 Free Recommended Connectors
Malpedia
Malpedia is a great all-around connector. It will add new malware names daily into the Arsenal section on OpenCTI along with enrichment of external references, indicators such as YARA rules, make relations with between malwares and threat actors, adding description and more.
The free version is great as is!
MalwareBazaar
MalwareBazaar connector is a tricky one. It basically adds any file that is uploaded to MalwareBazaar as indicators. There are two problems with that. Most uploaded files are not being linked to the Malware entities on OpenCTI and the connector is downloading and storing the malicious samples on your OpenCTI machine, so it might cost a lot of storage.
Although there are several flaws i recommend of modifying the connector code and fix these issues and you might have a really smart IOC feed, especially when you are able to link them to the Malware entities.
AlienVault
This is another great connector to use, it is free and only demands creating an AlienVault account and generate API Key.
The idea is that it will crawl over all the pulses you are subscribed to and import the data into your OpenCTI.
The downside is that you need to manually subscribe to new pulses constantly.
MITRE Att&ck
MITRE holds great knowledge about pretty “popular” cases, so we might find a lot of data regarding threat groups and campaigns with large scale.
In addition, it will import to the Attack Patterns section the MITRE table.
CVE
Straightforward and easy to use.
This connector simply imports information about CVEs into the CVE entity of OpenCTI so you will never miss a new CVE. The default setting is daily run but you can easily change it.
URLhous-recent-payloads
I think that is a great implementation of that the MalwareBazaar connector lacks. when it comes to URLhous, it is segregated into two different connectors. This connector is in charge of downloading the actual malicious payloads to your machine if you desire so you have more flexibility in storage management.
In addition, you can config what file type you are willing to download.
URLhous
This is the second part of the URLhous connectors that eventually import tones of IOCs for you to explore. Take into consideration that the tags that are found in URLhous will be added as tags to the Indicator or Observer Entity they will be created as – so linking to Malware entity or Threat Actor or Intrusion Set will have to be done by you.
URLscan
Great connector for tones of malicious URLs from all kinds – phishing, loaders, C2s, drop-zones, Tor nodes and much more!
Have fun and good luck!

