
The Art of Smuggling
We all love some C2 action. I though it’ll be a cool idea to list C2 and data exfiltration platforms i have witnessed lately. This is a good way to expand our knowledge and to see how threat actors are thinking out of the box.
Hosted Domain – Old School
So the more obvious and “classic” ways for malwares to exfiltrate data or receiving configurations. As much as this technique is obvious and simple to detect, threat actors still choose to use this technique with the understanding that this is technique has a very short life given the fact that once the domain is taken down or getting blocked by security vendors the campaign is basically gone.
Still, you can find this technique implemented on almost ANY malware out there.
Telegram
Telegram have became one of the most popular tools and platforms for threat actors to do pretty much anything.
From opening marketplaces to underground chats, leak channels and much more.
As Telegram provides many cool tools and features, it seems that the bots you can create on Telegram has really caught the eyes of threat actors in the past year or so.
It seems that malware campaigns that are using this platform are often use it to upload the obtained data from the victim’s machine to a bot that probably is programed to move it forward to an actual server that stores all of the victims logs.
In addition, it is also used for getting instructions and configurations (Figure 1).
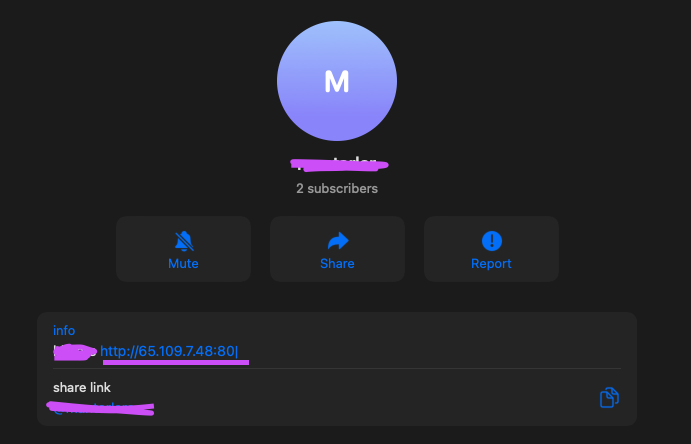
This allows threat actor to use the Telegram platform to change the C2 address periodically instead of relying only on one address that usually doesn’t live for too long.
Social Media
Social media is also a powerful tool for threat actors to manage and operate his stealers and malwares through an hard to detect platform.
Since the more popular social media making a hard time for fake accounts to stay a live for too long, threat actors migrated to other social media platform that are still legitimate but less popular such as Mastodon.
It seems that threat actors are using this platform to store a C2 address for their malware to find and follow which is another way to add flexibility and resilience to their campaigns by using fake profiles (Figure 2).
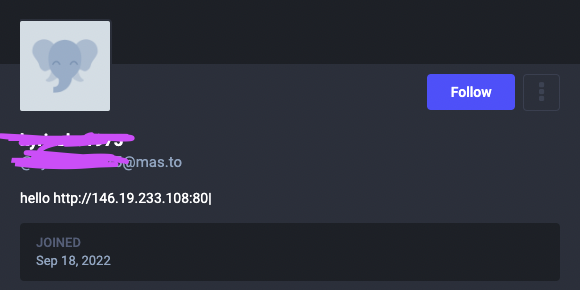
In addition, I have added a tool to my GitHub that can help you monitor these profiles if you find, and can scrap the new addresses once they change. Check it out!
Steam
Gaming platforms are another way. i think we all starting to understand the pattern here…
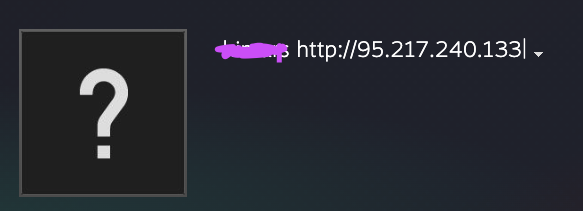
The idea is yet again to create a dummy account and putting C2 domains and addresses in the profile description for the malwares to find (Figure 3).
This is another case of Vidar using the steam community platform.
Conclusions
Now of course there are more ways to exfiltrate and receive data that is being used in campaigns, you can apply this technique on any legitimate platform, YouTube, GitHub, Spotify even? But i wanted to go over couple of the ways i have witnessed that is being used a lot.
The creativity never stops in this cat and mouse game.
Enjoy and Good luck!

